Session Initiation Protocol
[1] SIP is used in Internet telephony, in private IP telephone systems, as well as mobile phone calling over LTE (VoLTE).
[2] The protocol defines the specific format of messages exchanged and the sequence of communications for cooperation of the participants.
SIP was originally designed by Mark Handley, Henning Schulzrinne, Eve Schooler and Jonathan Rosenberg in 1996 to facilitate establishing multicast multimedia sessions on the Mbone.
[5] SIP was designed to provide a signaling and call setup protocol for IP-based communications supporting the call processing functions and features present in the public switched telephone network (PSTN) with a vision of supporting new multimedia applications.
It has been extended for video conferencing, streaming media distribution, instant messaging, presence information, file transfer, Internet fax and online games.
SIP has been standardized primarily by the Internet Engineering Task Force (IETF), while other protocols, such as H.323, have traditionally been associated with the International Telecommunication Union (ITU).
SIP is only involved in the signaling operations of a media communication session and is primarily used to set up and terminate voice or video calls.
The modification can involve changing addresses or ports, inviting more participants, and adding or deleting media streams.
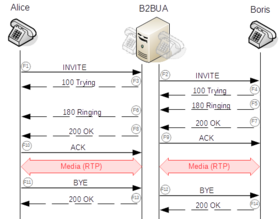
[10][11] SIP employs design elements similar to the HTTP request and response transaction model.
[12] Each transaction consists of a client request that invokes a particular method or function on the server and at least one response.
SIP reuses most of the header fields, encoding rules and status codes of HTTP, providing a readable text-based format.
The network elements that use the Session Initiation Protocol for communication are called SIP user agents.
Each of these service elements also communicates within the client-server model implemented in user agent clients and servers.
In SIP, as in HTTP, the user agent may identify itself using a message header field (User-Agent), containing a text description of the software, hardware, or the product name.
The user agent field is sent in request messages, which means that the receiving SIP server can evaluate this information to perform device-specific configuration or feature activation.
A proxy server primarily plays the role of call routing; it sends SIP requests to another entity closer to the destination.
Session border controllers (SBCs) serve as middleboxes between user agents and SIP servers for various types of functions, including network topology hiding and assistance in NAT traversal.
Several classes of responses are recognized, determined by the numerical range of result codes:[20] SIP defines a transaction mechanism to control the exchanges between participants and deliver messages reliably.
Invite transactions differ in that they can establish a long-running conversation, referred to as a dialog in SIP, and so include an acknowledgment (ACK) of any non-failing final response, e.g., 200 OK.
Such services may simplify corporate information system infrastructure by sharing Internet access for voice and data, and removing the cost for Basic Rate Interface (BRI) or Primary Rate Interface (PRI) telephone circuits.
[25][26] SIP-enabled video surveillance cameras can initiate calls to alert the operator of events, such as the motion of objects in a protected area.
The implementation can work in proxy server or user agent scenarios and has been used in numerous commercial and research projects.
SIP-I and SIP-T[29] are two protocols with similar features, notably to allow ISUP messages to be transported over SIP networks.
In contrast, the HTTPS protocol provides end-to-end security as it is done with a direct connection and does not involve the notion of hops.